NIST(National Institute of Standards and Technology)의 Computer Security Resorce Center 기술자료인 Special Publications 800시리즈 문서입니다.
첨부된 자료는 아래와 같은 일반적인 네트워크 구성 환경을 가정하에 네트워크 보안성 테스트 가이드 및 관련 툴에 대한 소개 등을 다루고 있다.
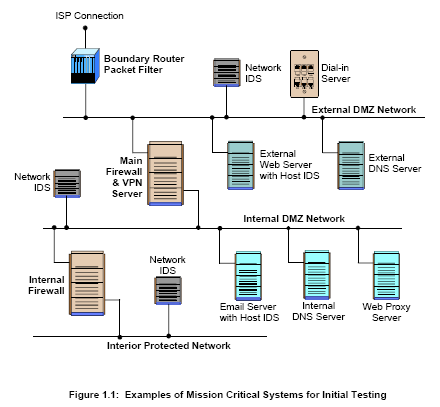
실제 실무 기술상의 테크닉을 다루고 있지는 않으나 개괄적인 개념의 이해 및 관련 툴을 이용하여 어떤 취약점을 테스트하는지에 대한 이해를 돕는 자료라 할 수 있다.
아래는 본 문서의 목차이다.
1. Introduction.....................................................................................................................1-1
1.1 Purpose and Scope........................................................................................................1-1
1.2 Definitions.....................................................................................................................1-2
1.3 Audience.......................................................................................................................1-3
1.4 Document Organization.................................................................................................1-3
2. Security Testing and the System Development Life Cycle..........................................2-1
2.1 System Development Life Cycle....................................................................................2-1
2.1.1 Implementation Stage....................................................................................................2-2
2.1.2 Operational Stage..........................................................................................................2-3
2.2 Documenting Security Testing Results..........................................................................2-3
2.3 Roles and Responsibilities.............................................................................................2-4
2.3.1 Senior IT Management/Chief Information Officer (CIO).................................................2-4
2.3.2 Information Systems Security Program Managers (ISSM).............................................2-4
2.3.3 Information Systems Security Officers (ISSO)...............................................................2-5
2.3.4 System and Network Administrators..............................................................................2-5
2.3.5 Managers and Owners...................................................................................................2-5
3. Security Testing Techniques..........................................................................................3-1
3.1 Roles and Responsibilities for Testing...........................................................................3-1
3.2 Network Scanning..........................................................................................................3-2
3.3 Vulnerability Scanning....................................................................................................3-3
3.4 Password Cracking........................................................................................................3-6
3.5 Log Reviews...................................................................................................................3-7
3.6 File Integrity Checkers...................................................................................................3-8
3.7 Virus Detectors...............................................................................................................3-9
3.8 War Dialing...................................................................................................................3-10
3.9 Wireless LAN Testing (“War Driving”)..........................................................................3-10
3.10 Penetration Testing......................................................................................................3-11
3.11 Post-Testing Actions....................................................................................................3-16
3.12 General Information Security Principles.......................................................................3-17
3.13 Summary Comparisons of Network testing Techniques..............................................3-19
4. Deployment Strategies for Security Testing.................................................................4-1 v
SP 800-42 GUIDELINE ON NETWORK SECURITY TESTING
4.1 Determine the Security Category of the Information System.........................................4-1
4.2 Determine Cost of Performing Each Test Type per System..........................................4-2
4.3 Identify Benefits of Each Test Type per System............................................................4-2
4.4 Prioritize Systems for Testing........................................................................................4-2
Appendix A. Terminology...................................................................................................A-1
Appendix B. References.....................................................................................................B-1
Appendix C. Common Testing Tools.................................................................................C-1
C.1 File Integrity Checkers........................................................................................................C-1
C.2 Network Sniffers.................................................................................................................C-2
C.3 Password Crackers............................................................................................................C-3
C.4 Scanning and Enumeration Tools......................................................................................C-4
C.5 Vulnerability Assessment Tools.........................................................................................C-6
C.6 War Dialing Tools...............................................................................................................C-7
C.7 Wireless Networking Tools.................................................................................................C-8
C.8 Host Based Firewalls..........................................................................................................C-9
Appendix D. Example Usage Of Common Testing Tools................................................D-1
D.1 Nmap.................................................................................................................................D-1
D.2 L0pht Crack........................................................................................................................D-8
D.3 LANguard..........................................................................................................................D-9
D.4 Tripwire............................................................................................................................D-11
D.5 Snort................................................................................................................................D-16
D.6 Nessus............................................................................................................................D-21
Appendix E. Index...............................................................................................................E-1
'Working > IT Security' 카테고리의 다른 글
| 무선랜 WEP 인증 해킹시연 및 방어대책 (1) | 2008.03.19 |
|---|---|
| Security Checklists (0) | 2008.03.02 |
| 해킹 시연 동영상 (0) | 2007.02.22 |
| Google, 개인정보유출이나 해킹의 도구로 활용된다. (5) | 2007.02.21 |
| 소스코드 검색엔진 All The Code Alpha 사이트 오픈 (0) | 2007.02.17 |
 invalid-file
invalid-file